Introduction
Picture this: a busy medical office buzzes with activity. A patient fills out an intake form containing his or her medical history, insurance details, and personal identifiers. Soon after, the form rests on the front desk—unattended and accessible to anyone who might stroll by. Hours later, a data breach occurs, and the Protected Health Information (PHI) is leaked. The repercussions? Fines of up to $50,000 per violation, a Department of Health and Human Services (HHS) investigation, and patients who may never return because trust is lost.
Patient intake is the key point of initial contact in healthcare, setting the tone for trust and care. Yet it’s the point at which PHI is most vulnerable. HIPAA exists to prevent just this kind of circumstance, mandating strict procedures for protected data. Failure can yield up to $1.5 million per annum in fines, lawsuits, and irreparable reputational harm.
This guide demystifies what is HIPAA, its role in safeguarding patient intake, and real-world steps to stay compliant. You’re a small clinic or a large hospital, but you must be aware of HIPAA compliance in the current healthcare landscape. Let’s dive into how you can protect PHI from the very first encounter.
Understanding HIPAA Compliance in Patient Intake
What Is HIPAA?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is an act aimed at computerizing healthcare information management. Its birth was driven by a requirement to make healthcare coverage portable with changing jobs for employees, which soon turned it into a benchmark of patient privacy. The HITECH Act of 2009 subsequently increased its bite by enhancing enforcement as well as penalizing breaches.
HIPAA’s main mandate? Safeguard PHI—any data that could be used to identify a patient, from names to diagnoses—throughout healthcare operations. It extends to covered entities such as physicians, hospitals, and insurers, as well as business associates like billing companies or software providers dealing with PHI. For patient intake, that means every form, electronic entry, or dialogue must conform to HIPAA standards.
HIPAA’s purpose is threefold: to provide data portability, fight fraud, and protect confidentiality. At intake, it regulates how you obtain insurance information, confirm identities, or document medical histories. A breach there—such as a stolen clipboard or compromised portal—can snowball into expensive repercussions.
For example, a 2018 breach at a major health system resulted in $16 million in penalties because of weak intake security.
Understanding what is HIPAA isn’t just regulatory trivia; it’s a roadmap to ethical care and legal protection. Next, we’ll break down its key rules and their intake implications.
Role of HIPAA Compliance in Patient Intake
The intake process is a high-risk stage for PHI exposure since it inevitably entails gathering sensitive information, such as insurance information for insurance verification, demographic identifiers, and medical histories. Typical risks consist of:
- Unsecured paper forms left unattended at front desks.
- Digital intake platforms lacking encryption or access controls.
- Staff errors like discussing PHI in public areas or mishandling consent forms.
A single breach during intake can lead to patient attrition because of damaged confidence, fines of up to $1.5 million per vi
Key HIPAA Rules Affecting Patient Intake
1. HIPAA Privacy Rule

Impact of HIPAA Privacy rule on Patient Intake:
- Consent Requirements: Patients must authorize PHI use for non-treatment purposes (e.g., marketing). Implied consent suffices for routine disclosures related to treatment or billing.
- Minimum Necessary Standard: Intake forms should only collect data essential for care. For example, omitting unnecessary fields like Social Security numbers reduces breach risks.
- Notice of Privacy Practices (NPP):Patients get this at intake, explaining their rights—like requesting record amendments. A sample NPP might read, “We protect your PHI and only share it as required for treatment or payment.”
Tip
Provide annual staff training on HIPAA Privacy Rule obligations, including recognizing permissible disclosures and securing written authorizations.
2. HIPAA Security Rule

Impact of HIPAA Security Rule on Patient Intake:
- Encryption: Digital forms and patient portals must use AES-256 encryption to protect ePHI during transmission and storage.
- Access Controls: Role-based access limits ePHI visibility. For instance, front-desk staff should not have access to clinical notes in EHRs.
- Audit Logs: Systems must track PHI access attempts, helping identify unauthorized activities during intake.
Example: A clinic uses an unencrypted tablet for intake. A hacker intercepts ePHI—game over.
Tip
IT teams and intake staff require cybersecurity training on phishing detection, password management, and multi-factor authentication (MFA).
3. HIPAA Enforcement Rule

The HIPAA Enforcement Rule outlines penalties for non-compliance, ranging from $100 to $50,000 per violation, depending on culpability.
Impact on Patient Intake:
- Breach Reporting: Practices must report unauthorized PHI access affecting 500+ patients to HHS and media within 60 days. Smaller breaches require annual reporting.
- Documentation: Maintain records of risk assessments, staff training, and breach responses for six years to demonstrate compliance during audits.
- Cases: In 2014, QCA Health Plan paid $250,000 after an unencrypted laptop with 148 patient records was stolen from an employee’s car.
- In 2016, North Memorial Health Care settled for $1.55 million after a laptop theft exposed 9,497 individuals’ ePHI.
- Cancer Care Group paid $750,000 in 2015 for a stolen unencrypted laptop, as noted in OCR records
Tip
Leadership teams need training on incident response protocols and breach notification timelines.
Challenges in HIPAA Compliance During Intake
1. Paper-Based Workflows
Depending on paper forms is dangerous—they can be lost, stolen, or even inappropriately thrown away. Moving to digital intake is safer and more effective. Utilize scanners with automatic delete functions so documents don’t stick around longer than they need to.
2. Unauthorized Access
Front-desk users occasionally view too much patient data, which generates more security vulnerabilities. To eliminate this, set up role-based access controls for your EHR system and run monthly access checks. This lets only the right individuals have the appropriate level of access.
3. Insecure Digital Tools
Not every digital solution is designed with security. Vendors for some do not have adequate encryption, exposing patient data. Always check Business Associate Agreements (BAAs) and ask for SOC 2 Type II reports to confirm your software vendors have rigorous compliance requirements met.
4. Identity Theft
Insurance fraudsters use compromised insurance information to seek out medical services, posing danger to patients as well as healthcare providers. This is overcome by implementing identity confirmation systems such as CERTIFY Health’s patient identification within web registration processes. Such added protection verifies the patients’ identities from the get-go.
Responding to a HIPAA Breach
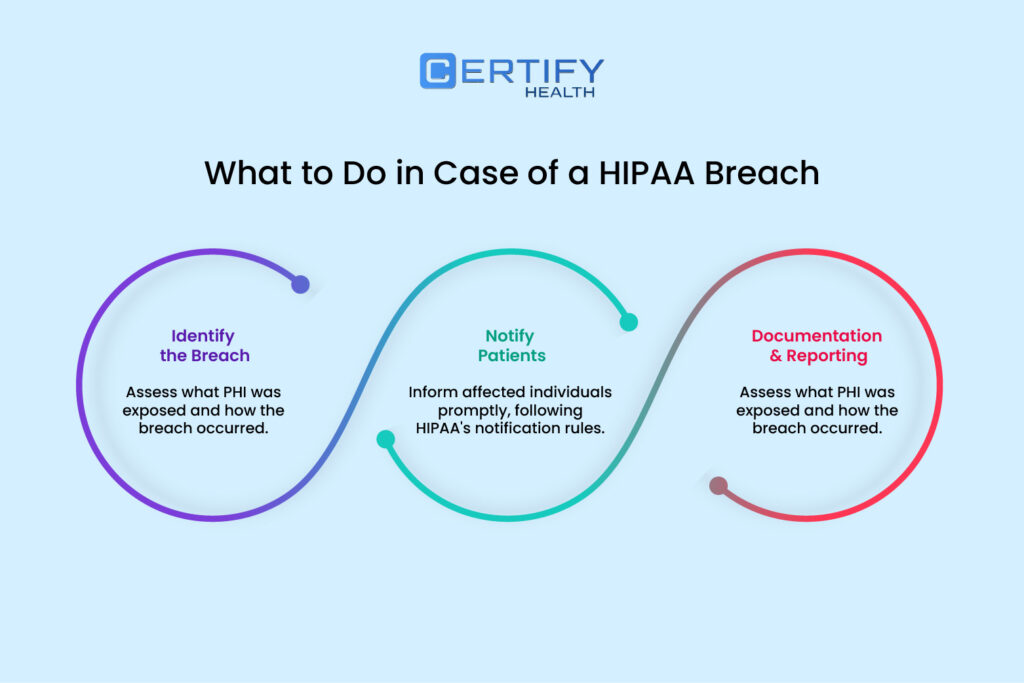
Step 1: Breach Identification
Conduct a below-given 4-factor risk assessment to determine if PHI was compromised leading to HIPAA Breach:
- Nature of PHI: Was sensitive data (e.g., HIV status) exposed?
- Unauthorized Recipient: Was PHI accessed by malicious actors?
- Acquisition Evidence: Are there logs showing data exfiltration?
- Mitigation Efforts: Was encryption or remote wipe used?
Step 2: Notification Protocols
- Patients: Notify affected individuals via mail/email within 60 days, detailing the breach scope and protective steps.
- HHS: Report large breaches (>500 patients) immediately via the HHS portal. Smaller breaches require annual submissions.
- Media: Issue press releases for breaches impacting 500+ residents in one region.
Step 3: Post-HIPAA Breach Remediation
- Update policies, retrain staff, and deploy advanced security tools like endpoint detection software.
- Document all actions for HHS audits, including revised risk assessments and training logs.
Practical Steps for HIPAA-Compliant Patient Intake

Designing Secure Intake Forms
- Minimize Data Fields: Collect only essential PHI (e.g., diagnosis-related information, not full employment history) to reduce breach impact.
- Digital Solutions: Use HIPAA-compliant platforms like CERTIY Health’s patient intake software, NexHealth or Tebra, which offer encrypted forms, e-signatures, and audit trails.
- Paper Form Protocols: Store physical forms in locked cabinets and shred them after digitization.
Securing Data Flows
- Multi-Factor Authentication (MFA): Require MFA for staff accessing patient portals, combining passwords and biometric verification.
- Private Intake Areas: Design waiting rooms with soundproof partitions to prevent eavesdropping on PHI discussions.
- Regular Risk Assessments: Conduct bi-annual audits to identify vulnerabilities like unpatched software or weak passwords.
Staff Training Strategies
- Phishing Simulations: Use mock emails to train staff on recognizing suspicious links or attachments.
- Scenario-Based Learning: Role-play PHI mishandling incidents, such as misdirected faxes, to reinforce secure practices.
- Sanctions Policy: Enforce penalties for repeated non-compliance, documented in employee handbooks.
Patient Consent and Authorization
- E-Signature Tools: Implement platforms like DocuSign for obtaining digital patient consent, ensuring patients review NPPs before signing: “I allow PHI use for treatment only.”
- Granular Authorization Options: Allow patients to opt into specific PHI uses (e.g., research) while restricting others.
Conclusion
HIPAA compliant patient intake is not optional for contemporary healthcare practices. By implementing encrypted digital forms, imposing strict access controls, and promoting a culture of security through staff training, organizations can reduce risks while increasing patient trust.
Systematic audits and preemptive breach readiness reinforce compliance further, making regulatory compliance a competitive strength. Emphasize HIPAA as not a bureaucratic obstacle but as the foundation of ethical, patient-focused care.
Also, read our Blog on: What Is Patient Intake? Why Digital Intake Is Better Than Traditional Methods











